The Influence of Effective Data Destruction on Cyber Security Threat Administration
The Influence of Effective Data Destruction on Cyber Security Threat Administration
Blog Article
The Importance of Effective Information Destruction Practices in Safeguarding Sensitive Info and Ensuring Computer System Safety And Security
In a period where data violations are increasingly common, the value of reliable data devastation methods can not be overstated. Organizations face considerable threats when sensitive details is improperly taken care of, possibly causing unapproved gain access to and severe economic consequences. Applying durable information devastation approaches not only reduces these threats but also aligns with lawful compliance needs, making sure that organizations promote their online reputation and foster client depend on. The inquiry stays: what details strategies can be utilized to improve these practices, and how can organizations efficiently incorporate them into their total cybersecurity framework?
Understanding Data Devastation
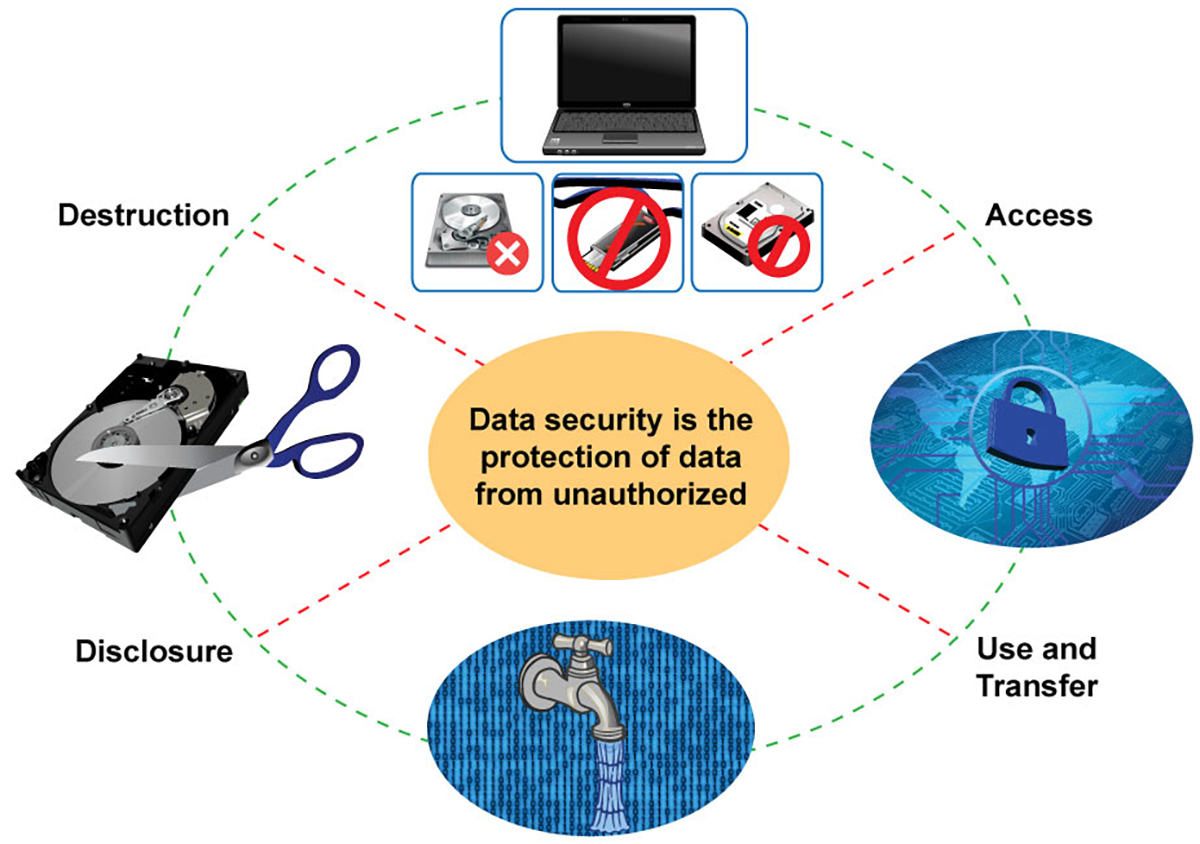
Recognizing data devastation is essential in today's electronic landscape, where sensitive info can conveniently be jeopardized. Reliable information damage entails not simply deleting documents but making certain that data is irretrievable through extensive techniques. This procedure is important for companies that take care of personal client details, intellectual residential or commercial property, or internal papers, as any kind of violation can result in severe economic and reputational effects.
Information devastation incorporates numerous methods, consisting of shredding physical media, degaussing magnetic storage tools, and using software-based remedies that overwrite data multiple times. Each approach offers a certain objective and must align with the level of sensitivity of the info being taken care of. As an example, physical devastation is typically chosen for difficult drives consisting of extremely personal information, while software application approaches may be sufficient for less sensitive information.
Furthermore, sticking to sector requirements and guidelines, such as the General Data Defense Law (GDPR) or the Health Insurance Policy Transportability and Accountability Act (HIPAA), is important for conformity and to alleviate lawful threats. Organizations must create a robust data damage policy, train employees on finest techniques, and routinely investigate their treatments to make certain that all sensitive info is disposed of firmly and successfully.
Risks of Inadequate Practices
Poor data damage methods subject companies to substantial dangers that can have significant consequences. When delicate info is not properly gotten rid of, it remains vulnerable to unapproved access, which can cause data violations and identification theft. Such incidents not only compromise the security of people but likewise tarnish the organization's online reputation, causing a loss of consumer depend on and potential monetary consequences.
Furthermore, governing compliance is increasingly stringent in lots of industries. Failure to abide by data devastation laws can result in hefty penalties and lawsuits against companies. These penalties can strain monetary resources and draw away focus from core company operations.
Furthermore, the abuse of recurring data can result in copyright burglary or company reconnaissance, jeopardizing affordable advantages (data destruction). The impact of insufficient data devastation extends past immediate monetary losses; it can additionally cause long-lasting damages to brand honesty and market setting

Organizations have to identify that information safety is not exclusively regarding stopping violations; it likewise includes the responsible administration of data throughout its lifecycle. Ignoring reliable information damage procedures can have disastrous ramifications, highlighting the necessity for durable measures to minimize these dangers.
Best Practices for Information Devastation
Executing reliable data devastation techniques is necessary for securing sensitive information and maintaining compliance with governing criteria. Organizations should adopt a multi-faceted strategy to make sure that information is irretrievable, consequently avoiding unapproved accessibility and potential violations.
First, data must be classified based on level of sensitivity, enabling companies to apply ideal devastation methods customized to the level of danger. For electronic information, utilizing software-based data-wiping tools that adhere to industry criteria can properly overwrite existing information. Physical devastation approaches, such as shredding or degaussing, view it are essential for gadgets that keep sensitive info, ensuring total eradication.
Establishing a clear information retention policy is crucial, detailing how much time different sorts of info should be retained before damage. Routine audits of data storage systems are likewise necessary to identify obsolete or unnecessary data needing elimination.
In addition, training staff members on the relevance of data damage and the details protocols to comply with fosters a society of protection within the company. Preserving documents of information damage processes provides responsibility and sustains compliance with exterior guidelines and inner policies. By adhering to these finest practices, companies can considerably mitigate the dangers related to information direct exposure.
Legal and Compliance Considerations
Failure to abide by these laws can cause extreme charges, consisting of substantial penalties and reputational damages. Organizations should carry out a robust data damage plan that lines up with these legal structures and gives clear guidelines on the appropriate approaches of data disposal, whether physical shredding or electronic cleaning.
Furthermore, preserving documentation of data destruction tasks is vital for showing conformity during audits or evaluations. By focusing on lawful and compliance considerations, companies can enhance their information safety and security posture and foster count on with stakeholders and clients, inevitably adding to an extra protected Read Full Report information administration environment.
Advantages of Effective Data Devastation
Effective information destruction practices extend beyond mere conformity; they provide significant advantages to organizations that prioritize them. By making sure that sensitive info is irretrievably destroyed, organizations mitigate the danger of information breaches and the prospective economic effects associated with them. This positive technique not just safeguards against unauthorized gain access to but also improves the general reliability of the company in the eyes of customers and stakeholders.
Implementing robust data destruction methods, such as physical destruction of storage devices or advanced data cleaning techniques, adds to the strengthening of a company's cybersecurity stance. data destruction. It decreases the probability of copyright burglary and protects exclusive info, therefore keeping a competitive side in the market
Final Thought
To conclude, reliable data damage techniques are necessary for safeguarding delicate info and boosting overall computer system security. By carrying out detailed methods such as degaussing, shredding, and software overwriting, organizations can mitigate the dangers connected with unapproved gain access to and data violations. Adherence to regulatory standards, consisting of GDPR and HIPAA, more reinforces conformity and safeguards against legal consequences. Inevitably, a commitment to robust information devastation techniques cultivates a culture of obligation, thus enhancing an organization's cybersecurity position and maintaining customer count on.
Report this page